Basic Cyber Security
How DO Passwords Get Hacked, Anyway?
The goal of a hacker is simply to get information, and unfortunately they have multiple tools at their disposal. However, with minimal caution and an understanding of basic online security, you can rest easier knowing you’ve really made them try to see your cousin’s wedding photos.
While little can be done on the user end about massive data breaches, there is a lot of time and energy spent on scamming individuals. Below are some common methods hackers will use to get personal logins.
Dictionary Attacks
Dictionary attacks are made using programs that will try to log in, or decipher a key by running through a full list of dictionary words. This is becoming less common, as more places have stricter password requirements. Annoyed by needing to add numbers and punctuation to your passwords? You’re not nearly as annoyed as the hackers still trying to use this method.
Alphanumeric passwords with punctuation are the best way to avoid this kind of attack. Simple passwords that are easy to guess will only make a hacker's life easier.
Phishing
Phishing is any attempt to gather personal information under false pretenses. Most phishing attempts are made via email, where a hacker will pretend to be a trusted entity such as PayPal, and send an official looking email asking for you to click a link and reset your password, or download something that may contain malware. If you’re not paying attention, you may not even know you’re being phished. Luckily, there are a few easy precautions to take.
First, look at the email header. Where is the email coming from, and who is it addressed to? If it is not sent to your exact email address, or if it comes from a domain name that doesn’t match the service, it is NOT legitimate.
One of the dead giveaways of a phishing attempt is terrible grammar. Let's take a look at one of these classic gems:
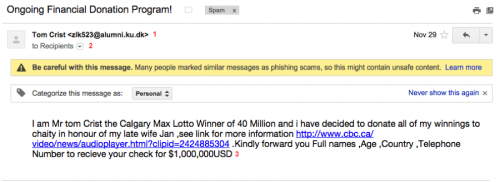
1. First of all, there is no reason Mr tom would have the email address above. Even if it were a legitimate University of Copenhagen account (it's not), those of you who had email in college would do well to remember that schools usually use the person's initials followed by a portion of a student ID number. Something smells… phishy.
2. To “Recipients” means it was blasted to an email list. Classic indication of spam and phishing. Even legitimate mass mailings, such as eNewsletters, will be delivered to your email address, specifically.
3. The complete lack of adherence to grammatical rules is a trick that is used to bypass spam filters (you will note that for this example, it did not work.) Also, the email makes absolutely no sense. Why would anyone need personal information to donate winnings to charity?
No matter how legitimate they look, do not click on links in these emails. They never lead anywhere good, despite their promises. And no, we’re not trying to keep the one mil for ourselves, we promise!
Little Things That Make a BIG Difference
An Internet connected device is like a car, in many ways. Both require a little know how and maintenance to safely get you where you’re going.
Keep Your Operating System Up To Date
We’re all guilty of ignoring all of the messages to update our operating systems. Newer Windows 8 machines even force the updates, eventually (it's like they know us!) However, keep in mind updates usually include security patches, and they’re for your protection. If you’re busy when you get an update notification, make a note of it, but don’t ignore it! Another good idea is to just pick one day a month as a “maintenance” day to make sure your software is up to date.
Use Different Passwords for Different Services
Many people use the same password for everything. It could be the most confusing password in the world, but if someone gets it, they will try it elsewhere. When data breaches happen, the attackers will get your password and email for an account, and they will see if you’ve reused the same login elsewhere.
Use AntiVirus Software
While AntiVirus software is not a magical guardian, it never hurts to run a monthly scan of your files to make sure nothing obviously nefarious is happening. This includes you too, Mac users! Anyone can get a virus. It's nothing to be ashamed of.
We know it’s a big scary world out there, but with a little bit of cyber security know how, you can rest pretty certain that no Nigerian princes will have your bank account information.

 An agency-eye view of Marketing, Advertising, Branding, Design & Media.
An agency-eye view of Marketing, Advertising, Branding, Design & Media.